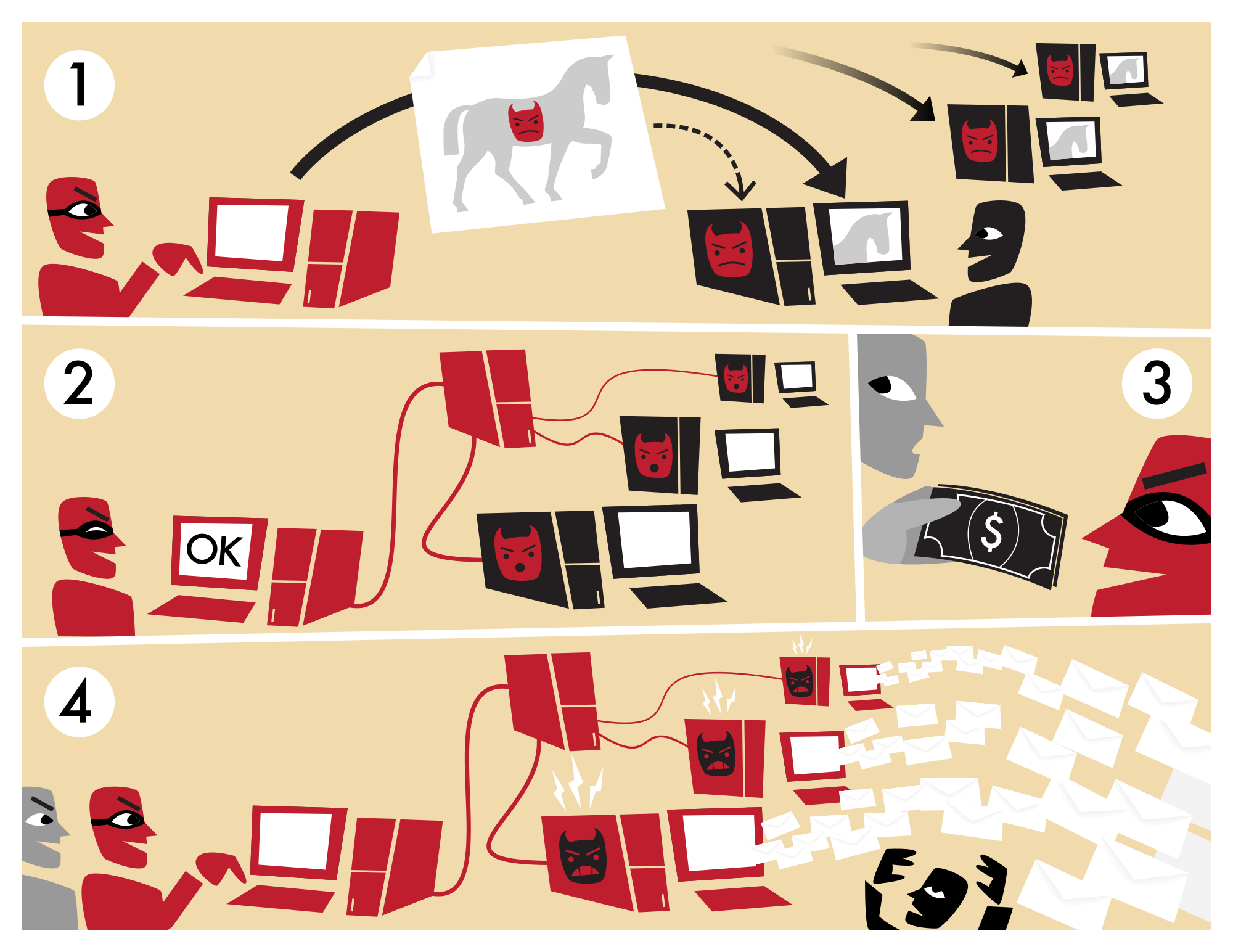
Product Item: How trojan store horse works
What is a Trojan Virus Trojan Horse Malware Imperva store, What is a Trojan Horse Virus Types Prevention in 2024 store, What Are Trojans How Can You Protect Yourself store, What is a Trojan Horse How Trojan Horse Malware Works store, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses store, What Is a Trojan a Virus or Malware How Does It Work Avast store, What are Banking Trojans GeeksforGeeks store, Trojan Horse Meaning Examples Prevention store, The Real Trojan Horse Infographic What Could the Real Trojan store, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet store, Understanding how trojan horse works in cyberattacks store, Trojan Horse Virus and Hacking PPT store, Source code for Skype eavesdropping trojan in the wild ZDNET store, How Trojan Horses Work HowStuffWorks store, What Is a Trojan a Virus or Malware How Does It Work Avast store, What is a Trojan Horse How it works Trojan Virus Definition store, What are Trojan horses A Trojan horse is full of as much store, What is a Trojan Horse What does the Trojan Virus do store, What is a Trojan Horse Virus Attack Littlefish Guide store, What is a Trojan horse How does it work store, Trojan Horse Virus History Types and Working store, What is a Trojan How this tricky malware works CSO Online store, What is Trojan Horse Computing zenarmor store, Trojan Horse Wikipedia store, The six stages of the Trojan horse strategy Download Scientific store, Understanding Chain Hacking A Guide to Botnets HuffPost Impact store, How to Tell if Your Computer Is Infected by a Trojan Horse store, Difference between Virus Worm and Trojan horse javatpoint store, how does Trojan horse works Explain Brainly.in store, How Trojan Horse Works How hacker creates payload Hacking store, What is a Trojan horse attack Shiksha Online store, What is a Trojan horse attack Shiksha Online store, What is Trojan Horse Malware and how can you avoid it store, Trojan Horses In Cybersecurity Training Ppt store, What is a Trojan Check Point Software store.
How trojan store horse works